Revolutionize SSH key and access management with browser SSH terminal
From software developers to infrastructure operations engineers, professionals across various domains rely on native terminal emulators such as GNOME, Terminator, Xterm, and others for their daily tasks. However, these tools fall short when it comes to handling SSH keys and access.
In the contemporary tech landscape, the SSH protocol stands as a cornerstone for countless tech teams worldwide. Driven by the ascendancy of cloud service providers like AWS (Amazon Web Services), GCP (Google Cloud Platform), and Microsoft Azure, as well as the rapid embrace of DevOps and SysOps methodologies, SSH usage has experienced exponential growth in the past decade. Let's delve into the multifaceted applications of SSH within the IT and software industry.
Leveraging SSH in IT and software tech industry
In the fast-evolving landscape of IT and software development, SSH (Secure Shell) has emerged as a linchpin technology, playing a pivotal role in ensuring security, connectivity, and efficiency. Here's a closer look at how SSH is instrumental in these domains:
- Cloud security and access: Major cloud service providers, including AWS, GCP, and Microsoft Azure, have entrusted SSH as the standard protocol for secure Linux/Unix server logins. This not only fortifies server access but also aligns with the best practices for security in cloud environments.
- Efficient deployment tools: Prominent Open Source deployment tools like Chef and Ansible heavily rely on SSH. Ansible, for instance, is wholly dependent on SSH for executing deployments, making SSH the backbone of automated provisioning, configuration management, and application deployment in DevOps workflows.
- Source version control: Git, the cornerstone of version control systems, utilizes SSH for secure data transport. It facilitates the secure exchange of source code changes between local repositories and remote Git servers. SSH encryption ensures the integrity and confidentiality of this data transfer.
- Extending SSH's reach: SSH's significance goes well beyond these examples. It extends to various facets of IT and software, from secure remote access to robust data transfer protocols. SSH has become a trusted tool in the arsenal of system administrators, developers, and DevOps engineers alike.
Challenges of SSH key management in native terminal emulators
In the realm of secure remote server access and data exchange, SSH (Secure Shell) keys have long been regarded as a robust authentication mechanism. They provide a secure and efficient means for developers, administrators, and IT professionals to access servers, transfer files, and manage remote resources. However, despite their effectiveness, the management of SSH keys within the confines of native terminal emulators presents a set of unique challenges.
As organizations increasingly rely on SSH keys for access control and data security, it becomes imperative to address the practical limitations encountered when employing these keys within standard terminal environments. In this discussion, we delve into the specific challenges that users face when managing SSH keys in native terminal emulators, exploring the intricacies of key distribution, security, access control, and the broader implications of these challenges on organizational efficiency and security posture.
- Manual SSH key distribution: Native terminal emulators often require manual distribution of SSH public keys to remote servers. This process can be error-prone and time-consuming, especially in environments with multiple servers and team members.
- Limited SSH key management: Native terminal emulators often lack integrated tools for efficient SSH key management. This can result in manual handling of SSH keys, making it difficult to organize, rotate, and revoke keys securely.
- Security risks of SSH key exposure: Using native terminal emulators for SSH connections can expose private SSH keys to potential security risks. Storing keys locally without encryption increases the chance of unauthorized access and compromises.
- Difficulty in revoking SSH keys: Revoking SSH keys when an employee leaves a team or a contractor's access expires can be challenging in native terminal emulators. Without a centralized SSH key management system, ensuring revoked keys are no longer used can be a complex task.
- Limited SSH access control: Native emulators cannot often enforce access controls on SSH keys effectively. Managing different access levels and permissions for various keys becomes challenging, increasing the risk of unauthorized SSH access.
- Limited audit trails, including SSH key auditing: Native terminal emulators may not provide comprehensive audit trails for SSH key usage, including SSH key auditing. This lack of visibility can hinder the detection of unauthorized SSH key usage, and suspicious activities, and may make it difficult to monitor SSH key-related actions effectively.
- SSH scaling challenges: As organizations grow, the complexities of managing SSH keys in native terminal emulators increase. What works for a small team may not be feasible at scale, leading to operational inefficiencies.
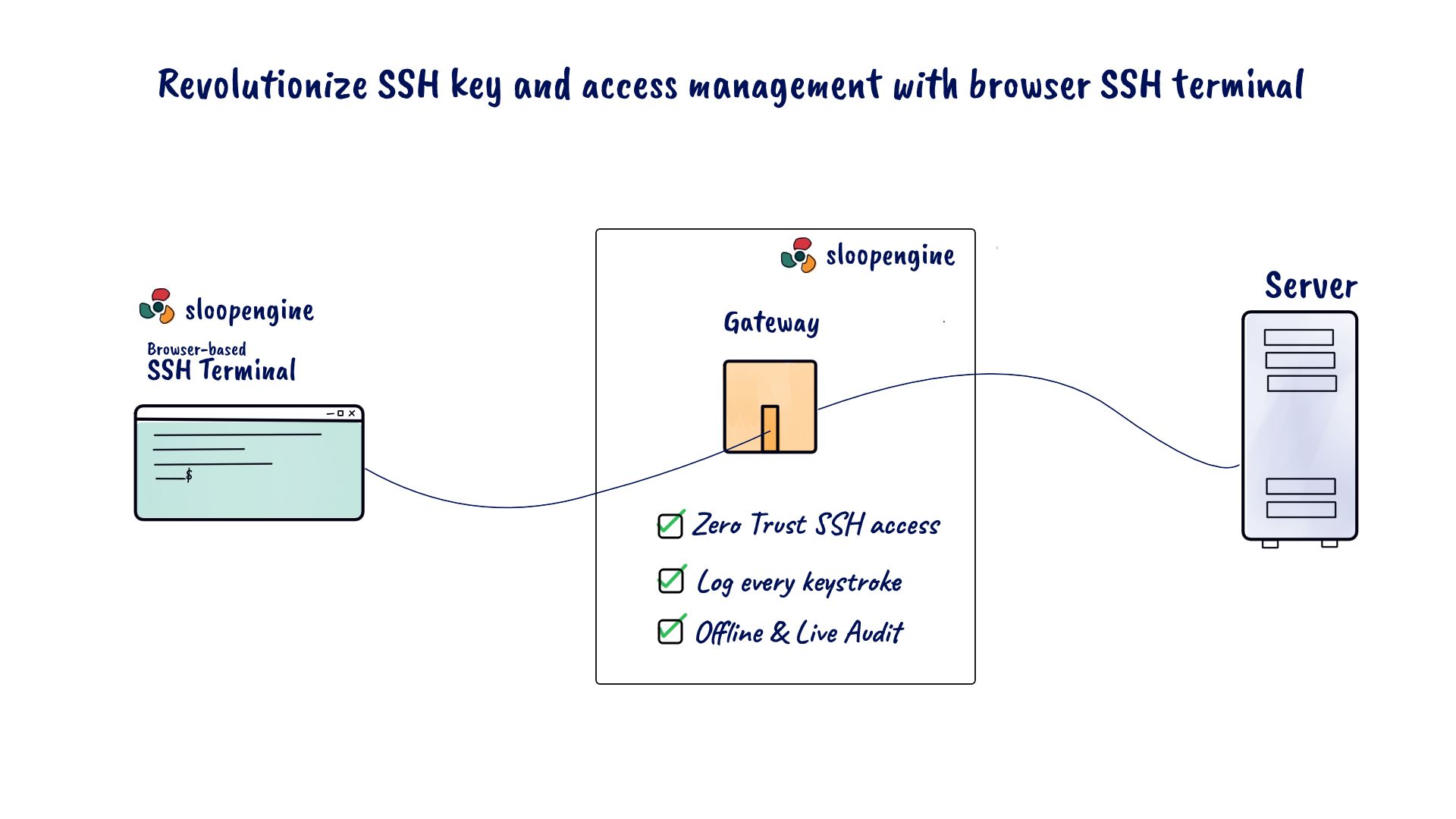
Solving challenges with SloopEngine's browser SSH terminal client
SloopEngine's browser SSH terminal client, coupled with robust SSH key management features, offers a solution. It empowers administrators to grant team members SSH access with a single click, eliminating the need to share the private key. This holds whether for on-premises servers or cloud servers like Amazon EC2, Google Compute Engine, and Azure Virtual Machine.
SloopEngine's SSH logging and auditing feature records every SSH connection from the browser terminal client to production servers. These logs are centralized and managed by SloopEngine, facilitating easy retrieval. The platform enables seamless tracking of users during SSH auditing, aiding in the identification of any anomalies or suspicious activities.
With live SSH auditing, SloopEngine empowers real-time monitoring of SSH connections initiated through its browser SSH terminal client. This capability enables oversight of team members' SSH sessions without their knowledge. Additionally, administrators can promptly terminate any potentially malicious connections with a single click.
In essence, SloopEngine addresses the limitations of native terminal emulators. Without a browser SSH terminal client, centralizing SSH access and enabling SSH logging, auditing, and more remains challenging.
SloopEngine, a cloud-based SaaS product, offers an array of key features tailored for tech teams, including centralized SSH key management, SSH access control, SSH logging and auditing, real-time SSH auditing, server-backed online IDE, project management, activity tracking, live chat, and more. All that's required is a standard web browser to leverage the power of SloopEngine.
Experience enhanced SSH management and security with SloopEngine's browser SSH terminal client - the bridge to streamlined, efficient, and centralized SSH operations.