Strengthen infrastructure security with SSH logging & auditing solution
The significance of SSH protocol cannot be overstated in the modern tech landscape. With the prevalence of cloud service providers like AWS (Amazon Web Services), GCP (Google Cloud Platform), and Microsoft Azure, coupled with the rapid adoption of DevOps and SysOps methodologies, SSH has emerged as the cornerstone of secure communication and access. This article delves into the pivotal role of SSH in the industry and provides insights into effective SSH logging and auditing practices, enabling you to better monitor SSH connections initiated by your team members.
The crucial role of SSH protocol in the IT/software industry
SSH protocol plays a pivotal role in various aspects of the IT/software industry.
- Cloud server access: Leading cloud service providers, including AWS, GCP, and Microsoft Azure, exclusively employ SSH protocol for Linux/Unix server logins, ensuring robust security for remote server access.
- Deployment automation: Prominent Open Source configuration management tools like Chef and Ansible heavily rely on SSH protocol for automated deployments. Ansible, in particular, hinges entirely on SSH for executing push-based deployment strategies.
- Source version control: Git, a paramount version control system, employs SSH protocol for secure source code transport. Git's internal mechanism utilizes SSH protocol during push/pull operations with remote Git repositories in GitHub, Bitbucket, GitLab, etc.
Understanding the necessity of tracking SSH connections
- Comprehensive security landscape: As cybersecurity threats continue to evolve, safeguarding sensitive data and critical infrastructure is paramount. SSH protocol plays a pivotal role in fortifying this security landscape, providing encrypted communication channels for data transfer and remote access. Effective SSH tracking ensures that any potential vulnerabilities or unauthorized activities are swiftly identified and addressed.
- Regulatory compliance: With the introduction of stringent data protection regulations such as GDPR, HIPAA, and PCI DSS, organizations are mandated to maintain rigorous controls over access to sensitive information. Proper SSH tracking facilitates compliance efforts by enabling organizations to demonstrate a strong commitment to data security through detailed auditing of all SSH connections.
- Internal governance and accountability: In large tech teams, where multiple individuals require access to various systems, maintaining a clear accountability framework is crucial. SSH tracking not only deters misuse of access privileges but also provides a trail of actions performed by each team member. This fosters a culture of responsibility and ensures that every action taken within the system is attributable to a specific individual.
Identifying the potential security risks with current SSH usage
- Lack of visibility: Without an effective SSH logging and auditing mechanism, organizations operate in the dark, unaware of who is accessing critical systems and what actions they are performing. This lack of visibility exposes businesses to both internal and external threats, making it essential to implement comprehensive SSH tracking.
- Inability to detect insider threats: Internal threats, often stemming from employees or contractors with privileged access, pose a significant risk. Insufficient SSH tracking leaves organizations vulnerable to insider attacks, where malicious actions can go unnoticed until significant damage has occurred.
- Failure to detect anomalies: In a dynamic IT environment, identifying anomalies and unusual behaviour is crucial to detecting potential breaches. A robust SSH tracking system can flag deviations from established access patterns, triggering alerts for further investigation and proactive risk mitigation.
- Complexity in incident response: In the event of a security incident or breach, the lack of detailed SSH logs complicates the incident response process. Organizations struggle to determine the extent of the breach, identify the root cause, and take corrective actions without comprehensive SSH tracking data.
- Risk to intellectual property: In tech companies, intellectual property and proprietary code are the lifeblood of innovation. Inadequate SSH tracking exposes these valuable assets to theft or unauthorized manipulation, potentially leading to a loss of competitive advantage.
- Stifling innovation: Without proper SSH tracking, organizations may become overly cautious, limiting the deployment of new tools or technologies due to security concerns. Effective tracking empowers organizations to innovate confidently while maintaining stringent security controls.
Introducing SloopEngine to revolutionize SSH management
To address these challenges, SloopEngine emerges as a game-changing cloud-based SaaS product. Offering a comprehensive suite of features, SloopEngine caters to modern tech needs, including online IDE, project management, SSH key management, SSH access management, SSH logging & auditing, activity tracking, live chat, and more.
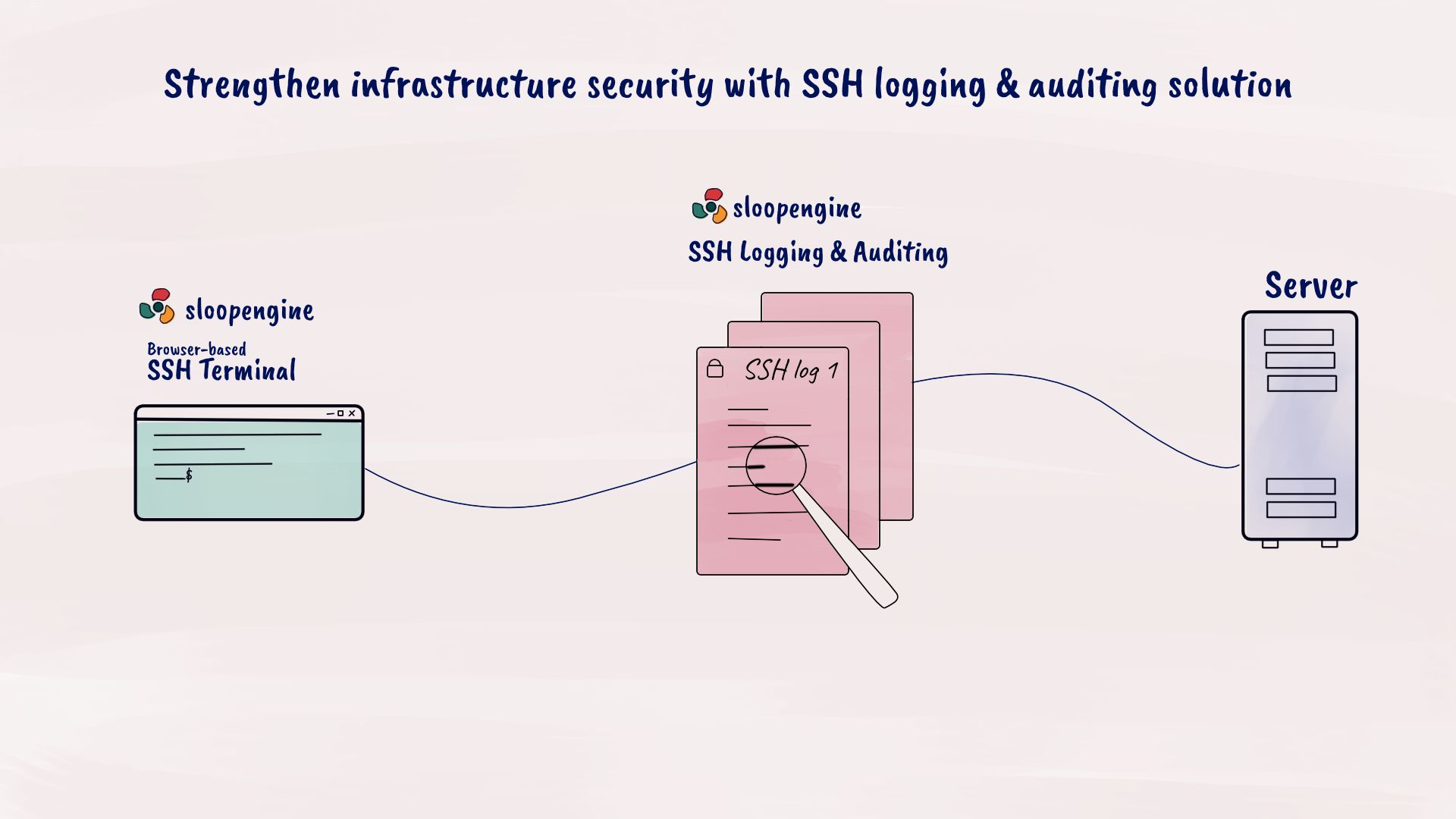
SloopEngine's SSH logging and auditing solution
With SloopEngine, logging and auditing your team's SSH connections becomes effortless and secure.
- Streamlined SSH access control: SloopEngine's browser-based SSH terminal enables you to grant or revoke SSH access with a single click, eliminating the need to share sensitive SSH private keys.
- SSH logging and auditing capabilities: All SSH connections made via SloopEngine's terminal are meticulously logged and recorded for auditing purposes. This comprehensive audit trail empowers you to swiftly pinpoint and address any unauthorized activities.
- Real-time SSH monitoring: SloopEngine goes beyond basic auditing by enabling real-time monitoring and live-streaming of ongoing SSH connections. Should any malicious activity be detected, you can terminate sessions instantly.
SSH protocol stands as a linchpin in the tech industry, driving secure communication and access across various domains. To harness its potential while mitigating risks, embracing effective SSH logging and auditing mechanisms is paramount. SloopEngine's innovative features empower organizations to manage SSH access seamlessly, enhancing security and accountability across the board. By adopting SloopEngine's advanced capabilities, tech companies can ensure a robust, secure, and streamlined approach to SSH management.
Would you like to explore the benefits of SloopEngine? Sign up today without any cost and experience the advantages yourself. We appreciate your interest in our platform. Thank you for considering SloopEngine.