Provide SSH server access without sharing SSH keys with team members
These days the SSH protocol is widely used by all kinds of organizations to provide SSH access to their servers running on-premises or on the cloud. Top-class open source automation tools such as Chef, Ansible, etc., heavily rely on SSH access to trigger deployments on servers. Even some organizations provide direct SSH access to Docker containers running on their production servers. Cloud services like AWS, Azure, GCP, Digitial Ocean, OpenShift, etc., enable SSH access to their cloud servers by default. Thus, SSH access is inevitable on any kind of infrastructure.
Traditional SSH key-based authentication for SSH access
The SSH protocol is designed to work as the client-server model, which requires the SSH client program to be installed on the local machine and the SSH server program on the remote server machine. To implement SSH key-based authentication you need to first generate an RSA or DSA key pair, which contains a private and public key file. The SSH public key has to be deployed within the user workspace on the server, whereas the SSH private key must be available on the local machine. Most organizations implement SSH access with SSH key-based authentication, the reason is SSH key-based authentication is more secure than SSH password-based authentication. But, the private SSH key sits on the local machine which is a security risk.
Security risks associated with SSH key-based authentication
By nature, you need to share private SSH keys with all team members who need SSH access to production servers. Even the use of SSH bastion hosts will only help you to provide centralized SSH access to production servers, but cannot protect your private SSH key. Your organization/business can be crashed in a second, if someone deliberately misuses the private SSH key. What will you do if,
- the private SSH key used to access production servers are copied?
- the laptop machine containing a private SSH key is lost or stolen?
- Do you forget to rotate SSH keys on your production servers?
A compromised private SSH key can put an end to your business in seconds.
Understanding the need for centralized SSH key management
It is very difficult for any growing organization to securely store, manage and rotate SSH keys which are used to provide SSH access for the team. With SloopEngine's centralized SSH key management, you can securely store, manage and rotate SSH keys for every environment such as production, staging, development and more. All the SSH keys that are managed using SloopEngine's centralized SSH key management are encrypted and stored. Due to the adoption of cloud servers, it's a must for any organization or team to centrally manage SSH keys because of the security risks associated with it.
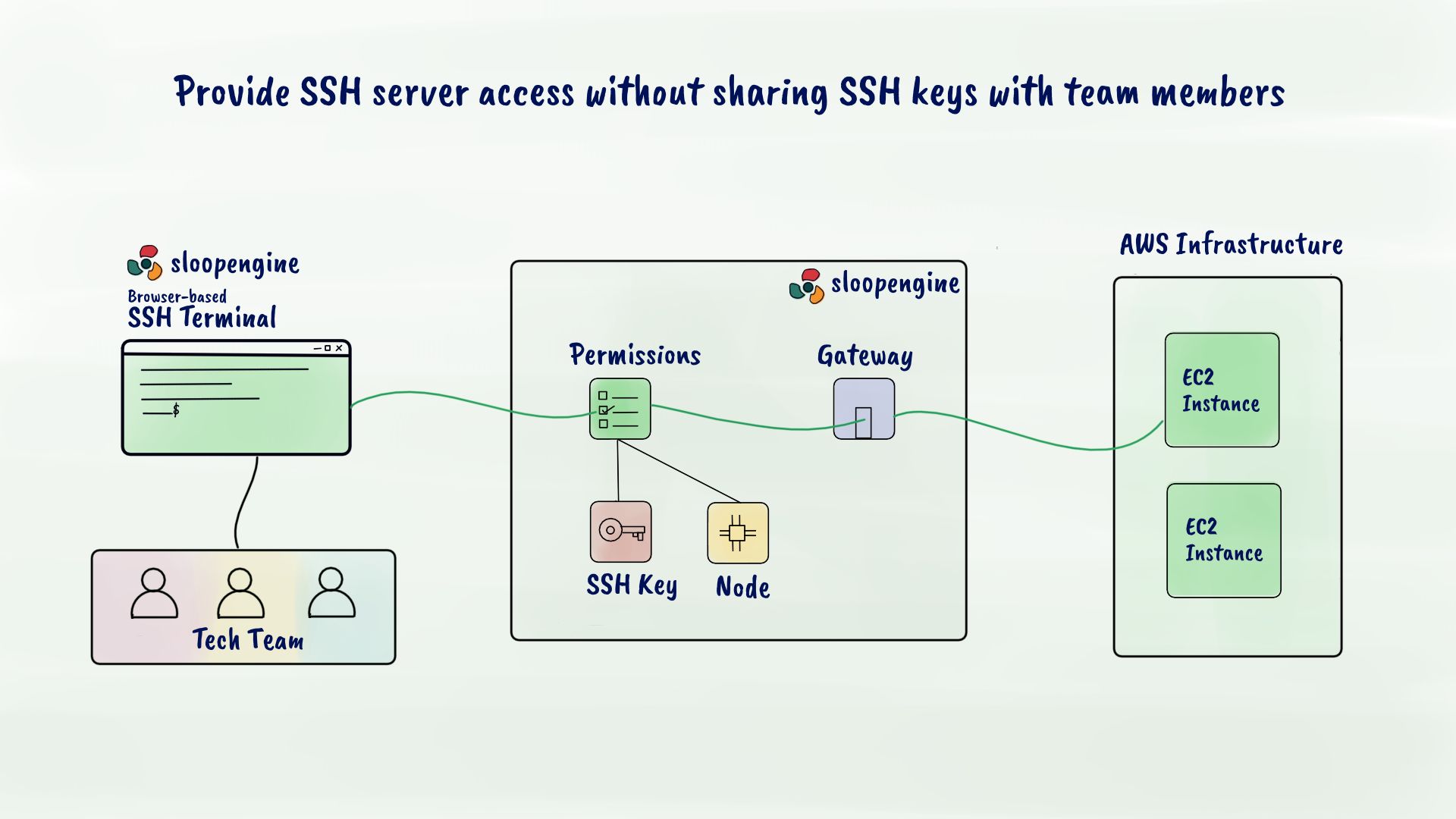
Provide controlled SSH access without sharing SSH key
Suppose you may have tens, hundreds or thousands of servers running on the production environment. Controlling SSH access for every team member becomes a complicated thing to manage as your team size grows. With SloopEngine's SSH access management feature, you can manage SSH access for every environment such as production, staging, development and more. Here you don't have to share the private SSH key with a team member to provide SSH access. SloopEngine uses its built-in secure web SSH terminal to establish SSH connection using SSH key-based authentication.